Platform for distributed web applications
Qworum is the Service Web
There are currently two different Webs that exist on the World Wide Web:
- The Document Web: This the Web that most Web developers will be familiar with. The primary type of content is the HTML page, and the primary content consumers are human users rather than machines.
- The Semantic Web: This the Web that is intended for machine consumption rather than human consumption. The primary type of content is RDF, which can be represented using many different but equivalent data formats such as JSON-LD and N-Quads.
Qworum adds another type of Web to the mix: the Service Web. Qworum is used for providing applications rather than content.
Qworum services are:
- Interactive: They can interact with end-users through HTML pages.
- Composable: They can call, and be called by, other Qworum services. A Qworum application is simply a special service endpoint that is supposed to run indefinitely, and does not normally receive or return data.
Note that Qworum is conceived as a superset of the Document Web. Although Qworum does not encompass the Semantic Web directly, it allows the use of semantic data as input & output for Qworum APIs, and for storing session data.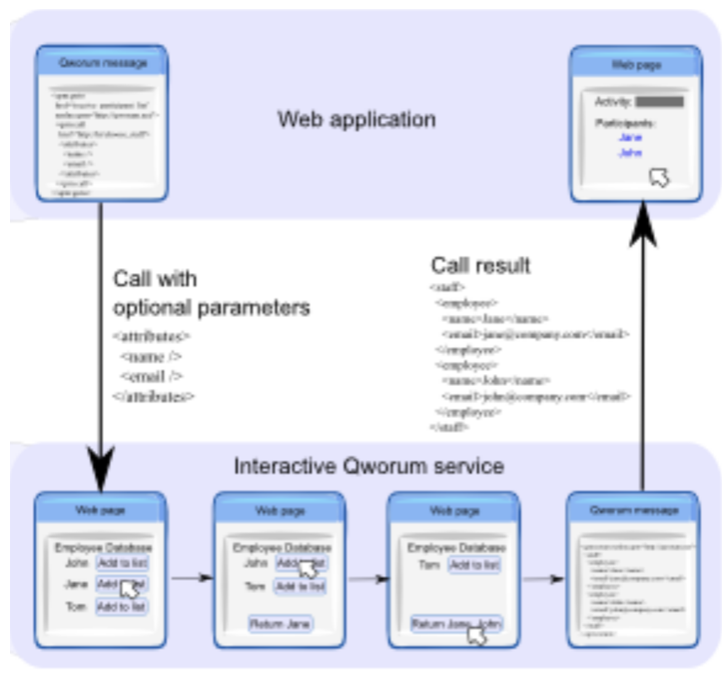
What is a full-stack API protocol?
Full-stack API protocols cover all three application layers — data, business logic, and presentation. 𝗤𝘄𝗼𝗿𝘂𝗺 𝗶𝘀 𝗰𝘂𝗿𝗿𝗲𝗻𝘁𝗹𝘆 𝘁𝗵𝗲 𝗼𝗻𝗹𝘆 𝗳𝘂𝗹𝗹-𝘀𝘁𝗮𝗰𝗸 𝗔𝗣𝗜 𝘁𝗲𝗰𝗵𝗻𝗼𝗹𝗼𝗴𝘆 in existence.
The biggest difference between Qworum and the other protocols is that Qworum structures and modularises application frontends, whereas the others are backend protocols.
In that sense, Qworum does not replace the other protocols, but complements them. For example, a Qworum endpoint may very well use REST for connecting to the service's backend.
It is also worth noting that Qworum is not only a protocol that web applications use for calling remote services, but 𝘄𝗵𝗼𝗹𝗲 𝗮𝗽𝗽𝗹𝗶𝗰𝗮𝘁𝗶𝗼𝗻 𝗳𝗿𝗼𝗻𝘁𝗲𝗻𝗱𝘀 𝗰𝗮𝗻 𝗯𝗲 𝗯𝘂𝗶𝗹𝘁 𝗳𝗿𝗼𝗺 𝘀𝗰𝗿𝗮𝘁𝗰𝗵 𝗮𝘀 𝗤𝘄𝗼𝗿𝘂𝗺 𝗔𝗣𝗜𝘀, and in fact this is the recommended way of structuring web applications. In this case, a web application will have a main Qworum endpoint, plus any number of local and remote endpoints that the application may call.
Another difference between Qworum and the other protocols is that Qworum sessions are stateful. This means that Qworum attaches runtime states to browser tabs.
A secure computing environment
The Qworum platform conforms to the same-origin policy that is the prevalent security mechanism for browser standards. In particular all phases of a given Qworum object are contained in the object's web origin. This ensures that data belonging to one web origin is unable to accidentally leak to another origin.

